Key Manager
The key manager provides functions to securely store keys, certificates, and sensitive data related to users and their password-protected APPs. Additionally, it provides secure cryptographic operations for non-exportable keys without revealing the key values to clients.
A key manager stores keys, certificates, and sensitive user data in a central secure repository. The central secure repository is protected by a password.
The main features of the Key Manager API include:
- Data store policy
A client can specify simple access rules when storing data in the key manager:
- Extractable or non-extractable
- Only for data tagged as extractable, the key manager returns the raw value of the data.
- If data is tagged as non-extractable, the key manager does not return its raw value. In that case, the key manager provides secure cryptographic operations for non-exportable keys without revealing the key values to the clients.
- Per key password
- All data in the key manager is protected by a user password.
- A client can encrypt its data using their own password additionally.
- If a client provides a password when storing data, the data is encrypted with the password. This password must be provided when getting the data from the key manager.
- Extractable or non-extractable
- User login
The user login control is implemented as follows:
- A user's database file is encrypted by the user's DKEK (domain key encryption key). A DKEK of a user is randomly generated and stored as encrypted with a user password when a user logs in for the first time.
- When a user logs in, the key manager decrypts the user DKEK with a user password. During the login session, any client can access the data which is protected by a user password. When a user logs out, the key manager removes the user DKEK from the memory.
- When a user logs in, logs out, or changes their password, the key manager must be notified. Only privileged APPs, such as LockScreen APP or Setting APP, can notify the key manager.
- When a user changes their password, the key manager re-encrypts the user DKEK with the new password.
- Data access control
By default, only the owner of a data can access to the data. If the owner grants the access to other applications, those applications can read or delete the data from the key manager database.
When an application is deleted, the data and access control information granted by the application are also removed.
Figure: Key manager process
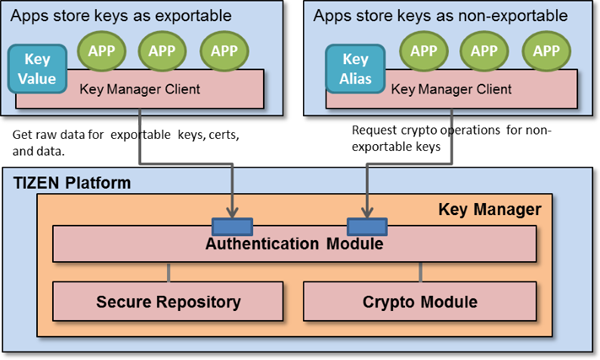
The key manager provides 2 types of APIs (in mobile and wearable applications):
- Secure repository APIs
All APPs can use the secure repository APIs to:
- Secure crypto APIs
The key manager provides the secure crypto APIs for the non-extractable keys and certificates to:


